A new virus spoofs Python digital signature to trick users into entering the back door.
Recently, Rising Security Research Institute captured a batch of malicious software with fake Python digital signatures. Attackers disguised these malicious software, induced users to download and run the Farfli backdoor program through websites and email links, and finally achieved the purpose of remotely controlling users’ computers and stealing private information.
Recently, Rising Security Research Institute captured a batch of malicious software with fake Python digital signatures. Attackers disguised these malicious software, induced users to download and run the Farfli backdoor program through websites and email links, and finally achieved the purpose of remotely controlling users’ computers and stealing private information.
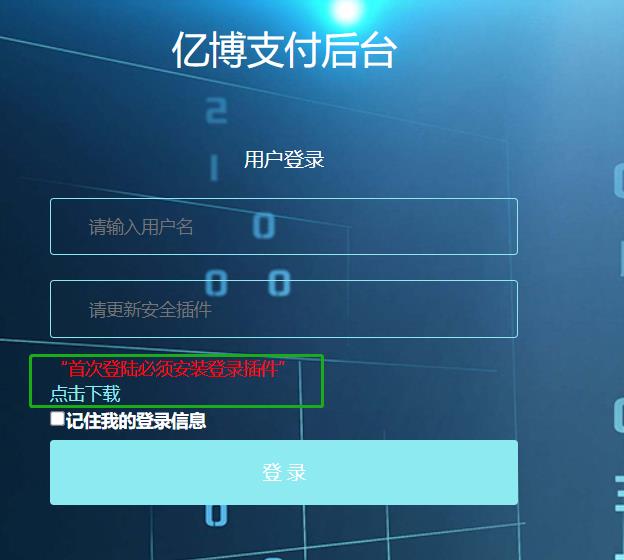
Rising security experts made a detailed analysis of the malware, and found that the malware with a fake Python digital signature appeared in a gambling payment website, which showed that "login plug-in must be installed for the first login", and when the user clicked, the malware would be downloaded.
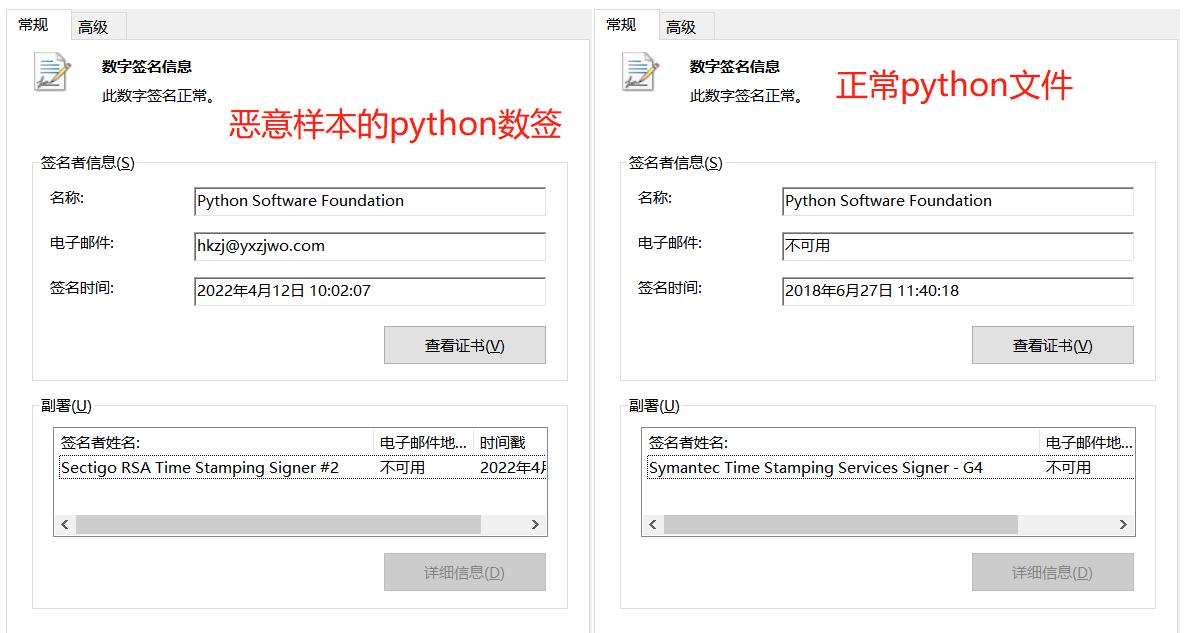
According to Rising security experts, this malicious software with a fake Python digital signature has a strong camouflage. The effective digital signature is very similar to the normal Python file digital signature. The names of the signers are Python Software Foundation, and only the email information is inconsistent, which is an address that has nothing to do with Python.
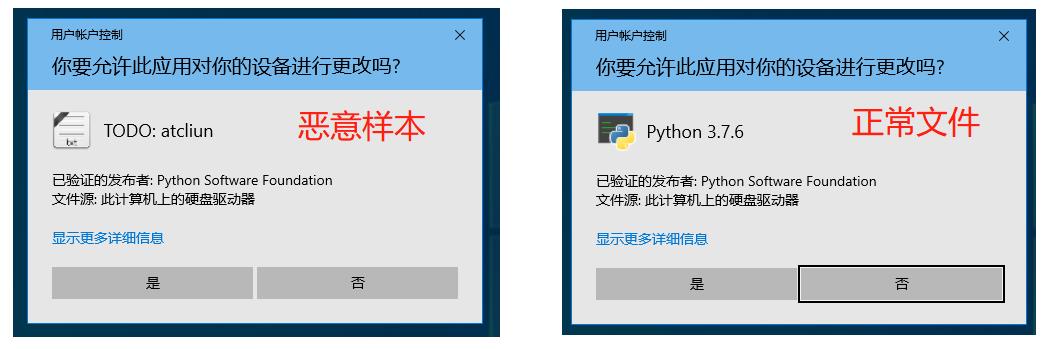
Moreover, when the user clicks to run the malware, its UAC pop-up window is not much different from that of the normal Python file, and only the signer name Python Software Foundation appears by default. Therefore, it is extremely difficult for users to judge whether this file is normal by digital signature.
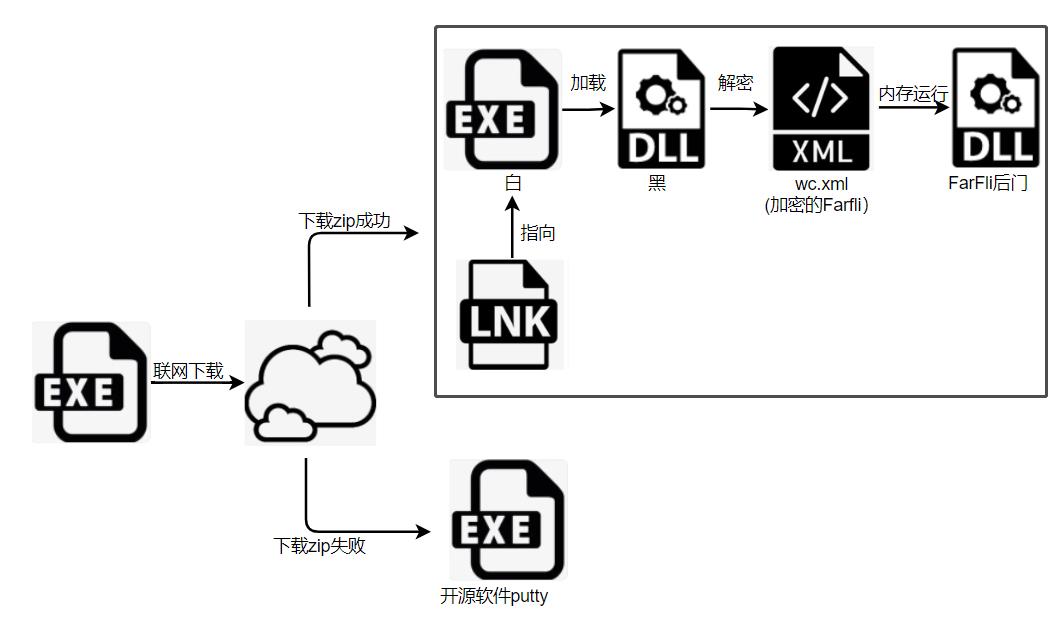
Rising security experts said that these confusing operations in the early stage were only the foreshadowing, and the attacker’s ultimate goal was to let the user download the compressed package with the remote control Trojan in Youdao cloud notes through this disguised malicious program, and the compressed package contained normal exe files, dll malicious files and encrypted Farfli backdoor programs. Therefore, as long as the user clicks execute Exe, the dll will be loaded, which will decrypt the Farfli backdoor program and make it run secretly in the memory, and the user’s computer will face the risks of file theft, remote control, keyboard recording, camera being viewed and so on.
Because the malicious software of this fake Python digital signature is very disguised and difficult for users to distinguish, Rising security experts remind users to pay attention to the following points:
1. Don’t open suspicious files
Do not open suspicious files and emails from unknown sources to prevent social engineering and phishing attacks.
2. Deploy gateway security products such as network security situational awareness and early warning system.
Gateway security products can use threat intelligence to trace the threat behavior track, help users to analyze the threat behavior, locate the source and purpose of the threat, trace the means and path of the attack, solve the network threat from the source, find the attacked node to the maximum extent, and help enterprises to respond and deal with it faster.
3. Install effective antivirus software to intercept and kill malicious documents and Trojan viruses.
Anti-virus software can intercept malicious documents and Trojan viruses. If users accidentally download malicious files, anti-virus software can intercept killing, prevent viruses from running, and protect users’ terminal security. At present, Rising ESM anti-virus terminal security protection system can intercept and kill such malicious software, and users can install and use it to avoid risks.
4. Install system patches and important software patches in time.
Many malicious software often uses known system vulnerabilities and software vulnerabilities to spread, and installing patches in time will effectively reduce the impact of vulnerability attacks.
5. Use strong passwords instead of weak passwords such as "123456", especially for devices that are open on the external network.
Weak passwords, like vulnerabilities, are often used by attackers and malware to spread and invade, and using high-strength passwords will block this attack.